Hackers Promise ‘No More Healthcare Cyber Attacks’
As leading cybercrime gangs promise not to attack healthcare organizations during the COVID-19 pandemic, can we take them at their word?
The coronavirus pandemic continues to bring out the best in so many people as individuals, communities and businesses combine in the fight against COVID-19. It has also exposed the worse sides of some, from those clearing the supermarket shelves and preventing vulnerable people from getting the supplies they need, to profiteering companies. Then there are the cyber-criminals exploiting fear and the need for information to spread malware and defraud victims. But could the criminals be having a change of heart? The cybercrime groups behind two of the most prolific ransomware threats have issued statements that they will not attack healthcare and medical targets during the coronavirus crisis. The problem with this is twofold: can you take a criminal gang at their word, and can they prevent healthcare organizations from getting caught in the attack crossfire even if they wanted to?
The COVID-19 ransomware threat
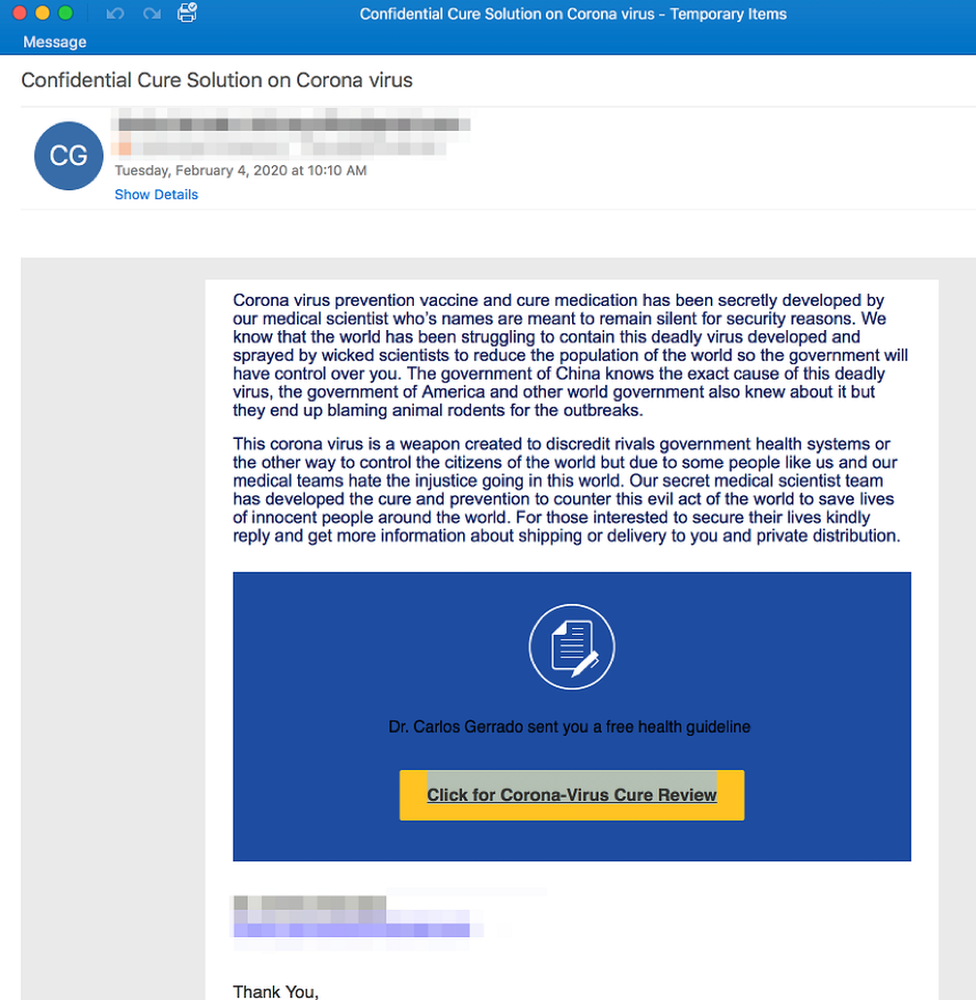
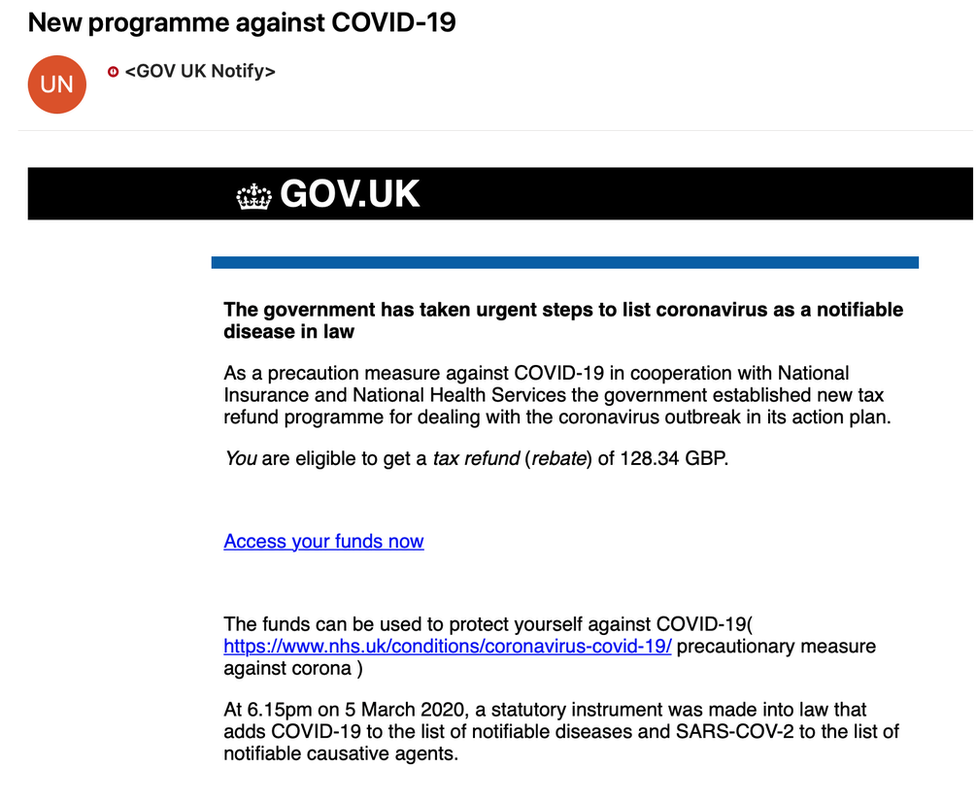
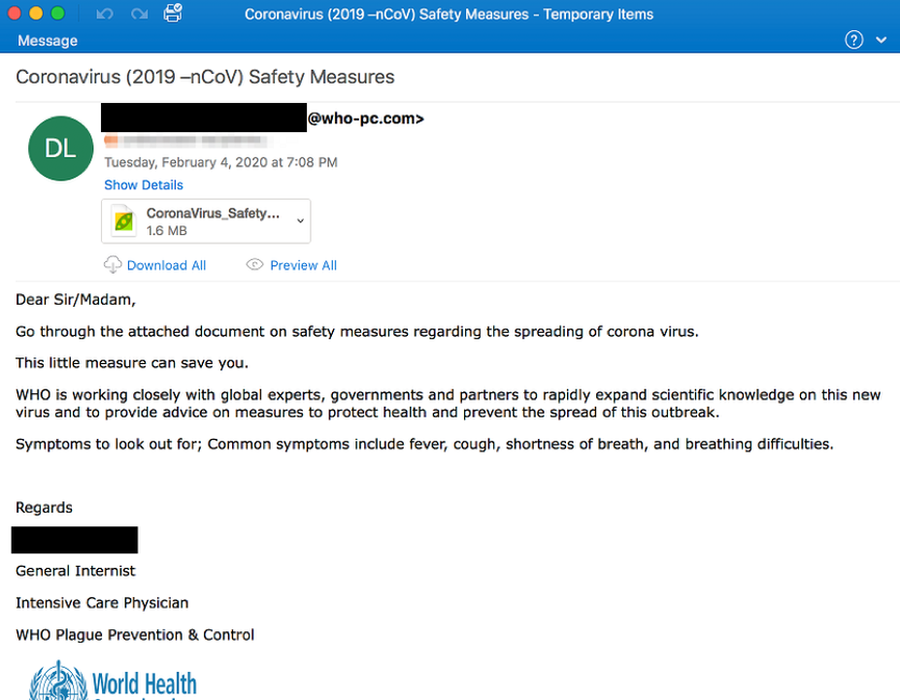
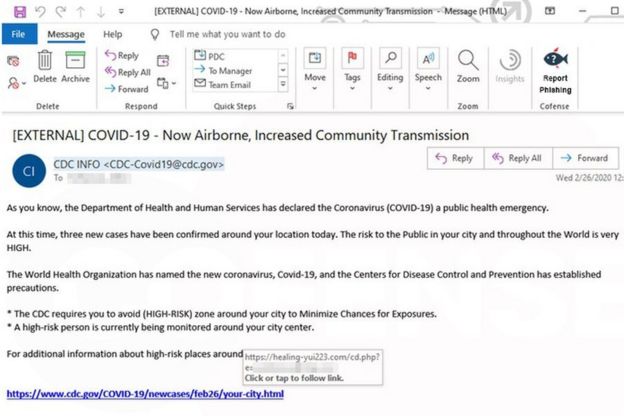
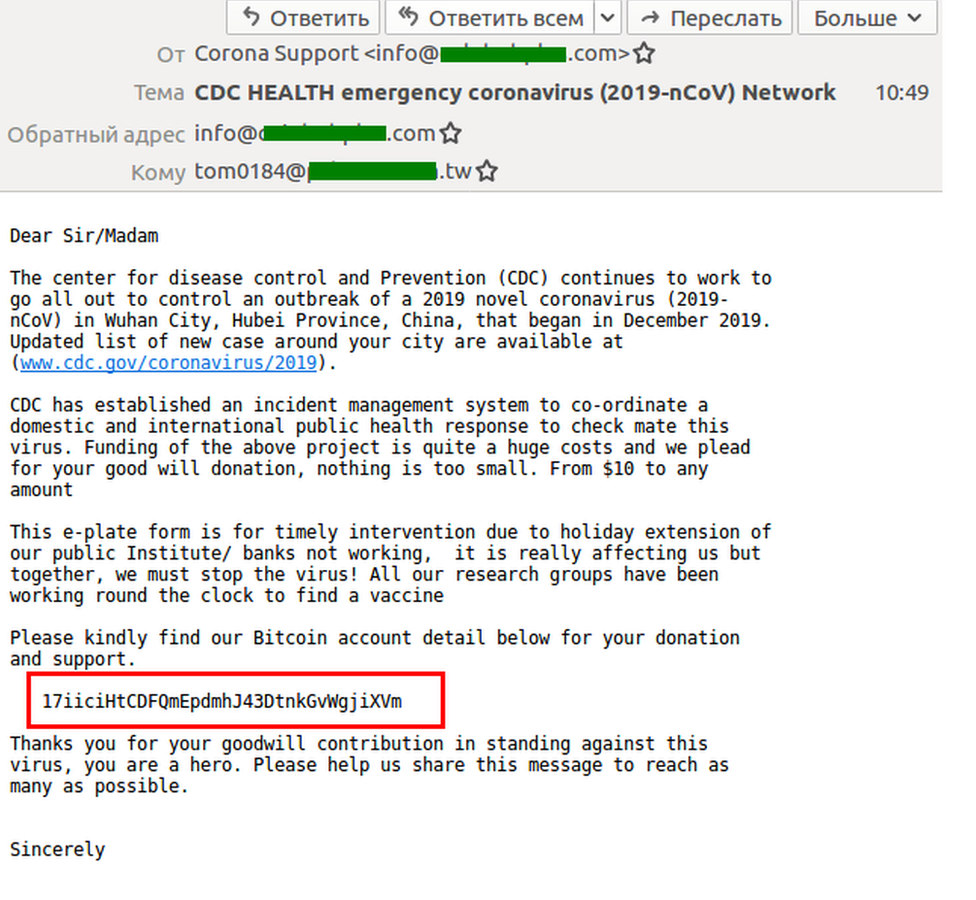
Ransomware continues to be one of the most severe threats facing organizations of all kinds, especially as attack methods continue to evolve. Like any criminal enterprise, the gangs behind the operation of ransomware will exploit current concerns to infect victims. The coronavirus pandemic is, sadly, not exempt from this. We’ve already seen COVID-19 infection distribution maps laced with malware, and the U.S. Attorney, Scott Brady, has warned people to be wary of an “unprecedented” wave of coronavirus scams.
Ransomware cybercrime gangs promise to give healthcare a free pass
Lawrence Abrams, the creator of BleepingComputer, reached out to the cybercrime groups behind the operation of some of the most prolific and dangerous ransomware threats. Abrams asked a simple question: will you continue to target health and medical organizations during the COVID-19 pandemic? At the time of writing, two had replied and their answers might surprise many readers. The first to respond were the operators of the DoppelPaymer ransomware threat, who told Abrams that they “always try to avoid hospitals, nursing homes.” When attacking local government targets, they “do not touch 911,” although sometimes emergency communications are hit due to network misconfigurations.
Interestingly, the DoppelPaymer cybercrime group has said that if a medical or healthcare organization does get hit by mistake, then it will provide a free decrypter code. “If we do it by mistake, we’ll decrypt for free,” the threat actors said, although pharmaceutical companies are not included in this ransomware amnesty. “They earn a lot of extra on panic,” the criminals said, adding that they have “no wish to support them.”
DoppelPaymer is an example of what Microsoft refers to as human-operated ransomware, causing havoc with ransom demands that use exfiltrated data as leverage. This is where the promises not to target health organizations fall a little flat; the risk to third parties remains. Ask Lockheed Martin, SpaceX and Tesla who were victims of the kind of collateral damage that DoppelPaymer can cause. Although not infected by the ransomware themselves, sensitive documents belonging to them and exfiltrated from a parts supplier, which did fall victim, were published by the cyber-criminals.
Maze ransomware criminals confirm they will stop attacking medical organizations
The operators of the Maze ransomware threat also said they would stop attacking medical organizations until “the stabilization of the situation with the virus.” The Maze actors did not confirm whether a decrypter would be available if healthcare organizations are infected unintentionally. However, security vendor Emsisoft, in partnership with incident response outfit Coveware, emailed me to confirm that it will be offering a completely free of charge ransomware recovery service to critical care hospitals and other healthcare providers. This includes the development of a decryption tool where possible.
At the time of writing, there has been no such promise from the criminals behind the Ryuk threat. Ryuk was the ransomware that recently took down North Carolina city and county government systems, and led to the City of New Orleans declaring a state of emergency as 2019 came to an end.
Self-preservation and not altruism
“If this announcement from ransomware operators, also known as cybercriminals, is accurate, it is motivated by self-preservation and not altruism,” Ian Thornton-Trump, CISO at Cyjax, says. He bases this on the fact that the law-enforcement response to any such attack during a time of crisis like this would be “overwhelming.” And that’s before even considering the military and intelligence agency resources that could be thrown at criminals attacking critical healthcare targets during a pandemic. “The last thing cybercriminals want is an APT actor’s offensive capabilities deployed against them,” Thornton-Trump told me, “a particularly spectacular and effective ransomware attack may even elicit military action up to and including a special forces mission to take out the actors responsible for the cyber-attack.”
The criminals promise could be hard to implement in the real world where external facing IP addresses will not necessarily identify a target as being a healthcare organization, or part of the critical supply chain that supports one. “The delivery of health care from drugs, lab work to medical equipment such as N-95 masks or Brew Dog’s re-tooling to produce a product like a hand sanitizer,” Thornton-Trump explains, “involves a multitude of critical supply chain relationships: I fear that the criminals lack the knowledge of how multi-faceted health care delivery is and what organizations deliver the health care services.”
Thornton-Trump has some stark advice for those cyber-criminals: “shut down operations completely for the duration of the coronavirus pandemic, lest you draw the ire of an angry nation with significant cyber capabilities of their own.”
Jake Moore, a cybersecurity specialist at ESET, warns that considering these promises, “we mustn’t get complacent as there are thousands of threat actors, each with a different level of conscience and ethics.” Even if these groups that responded, he argues, can be trusted, “that doesn’t mean the health sector should take their eye off the ball for any moment. Don’t forget that WannaCry crippled the NHS without any thought of the impact on the country and cost to the industry.” And WannaCry wasn’t even targeting healthcare; the NHS was just collateral damage.
We’re Cloudscape.
We believe you should have the best backup solutions for your business.
We’ll get to know your business and determine the most appropriate solution to meet your technical requirements while being commercially sensible in cost and productive with time.
If you feel that your data isn’t being backed up correctly, please get in touch.