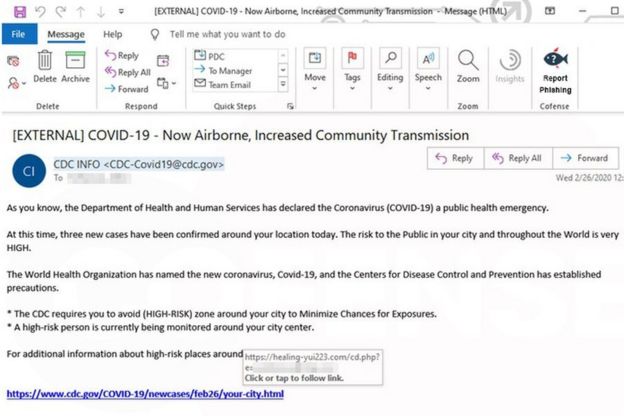
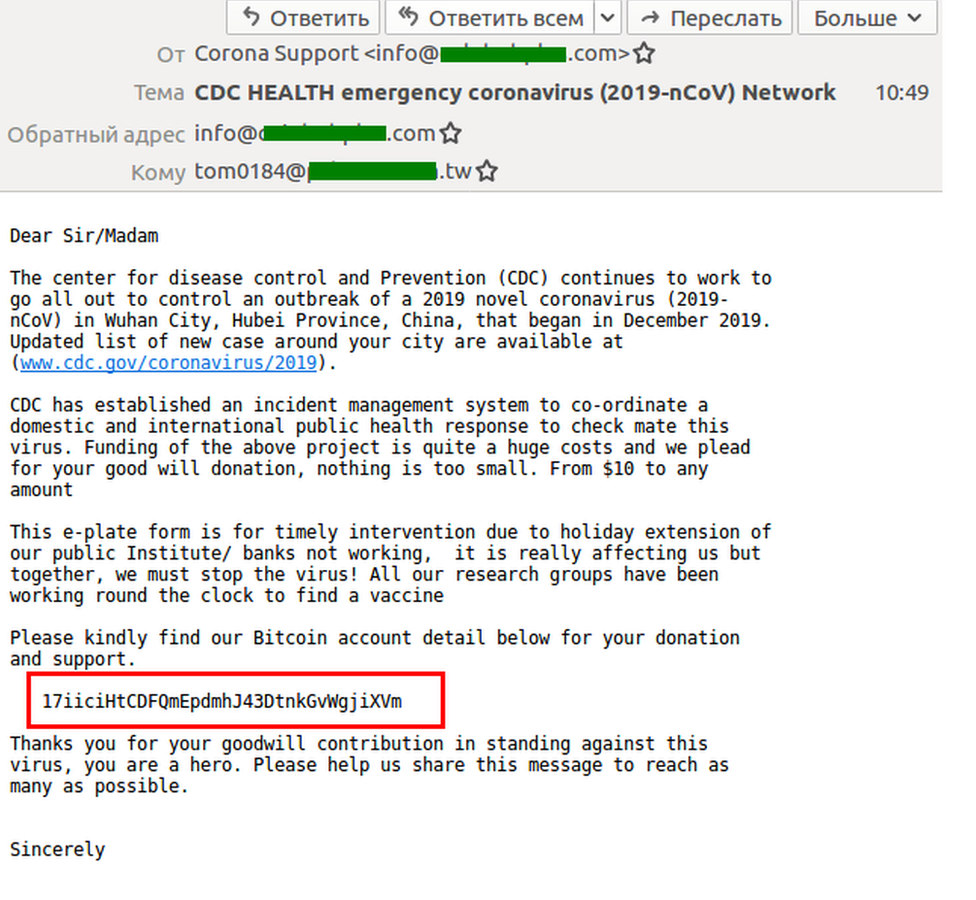
The Fort of Cyber Security – What is Smishing?
Pull up the drawbridge and protect your business from Smishing
But what exactly is Smishing?
The word ‘Smishing’ originates from both ‘SMS’ and ‘phishing’ combined. Phishing is the trickery of using imitation to get you to reveal personal, sensitive, or private information.
However, instead of using email, normal phone calls, hoax websites or VoIP, Smishing is carried out through text or SMS messages.
In similarity to both Phishing & Vishing, Smishing also uses a vast selection of scare tactics and emotional manipulation to trick you into giving up your information. The goal of is simple and exactly the same: To steal your money, your identity, or both.
Why is Smishing so perilous to my business?
Your private information needs to stay private, with a simple text message, that could all go up in flames.
Build a moat around your data and learn how to protect it, here are a few key tactics of Smishing:
The use of Social engineering – Leveraging your trust in order to obtain your private information
The threatening approach – “If you ignore this message you will be charged daily until you accept the terms”
Links & attachments (malicious) – Simple but effective, send 1000 texts with a single link, someone’s bound to click it
Along with various amounts of siege tools available, cybercriminals have an endless number of tricks to get your information.
How do you prevent Smishing attacks?
Everyone receives texts on a daily basis, most of the time they are from your friends, family or a legitimate source. But, every once in a while, you’ll be targeted by an anonymous number. To help you remain vigilant, below are some specific steps to prevent Smishing:
– Never reply to unknown numbers unless you are 100% confident it’s trustworthy
– Don’t reply to text messages riddled with errors & mistakes.
– Don’t click on any links or attachments within a text message.
– Never install applications that come through a text message, verify things first but always stick to the app store.
– If the preview looks dodgy, don’t even open it, just delete it.
Also, in order to maximise security for your mobile phone, we recommend a VPN. A Virtual Private Network will secure and encrypt any communication taking place between your mobile and the Internet on the other end. Therefore, giving you an extra layer of protection.
** Get your FREE pinpoint guide on Smishing below **
We’re Cloudscape.
We believe you should have the best backup solutions for your business.
We’ll get to know your business and determine the most appropriate solution to meet your technical requirements while being commercially sensible in cost and productive with time.
If you feel that your data isn’t being backed up correctly, please get in touch.